The Safest Way to Communicate Isn't What You Think
the internet is not your friend
The safest way to communicate is to go out in the woods far away from all electronics and whisper in someone’s ear. No one can hear you and you know the message was received.
That might be safe, but it isn’t practical for those not in close proximity to the other person — after all, if someone was down the hall, you could just walk over and say hello. For the rest of us, communications technology is quite handy and immediate when we are at a distance. The safest way for us to communicate is over a private network, away from the internet.
A private network isolates you from the internet and its many threats while prevent censorship of your valuable communications and helping protect your financial transactions.
Your typical VPN and “secure messenger” over the internet - they aren’t everything they are promoted to be as you will see. What can you do about this? We’ve been working hard on developing a tech solution we call Private Line.
Please Take Our Survey so we can Build the Safest Way to Communicate (that’s publicly available). It takes less than 5 minutes and your answers are confidential. We appreciate your help!
CLICK HERE
Is Encryption Secure?
Sure it’s secure…if you are trying to keep out the local high school hacker and maybe low level criminal gangs. Use logic. If encryption was so secure that “they” could not get into it, would “they” let you have it? No. Encryption needs to be strong enough to keep certain threats out but allow certain security agencies to have full transparency of everything. Otherwise encryption could be used like a weapon (against people like WEF Prof. Schwab and his friends). Here is how they think:
“In this new world, we must accept transparency, and I’ll even say total transparency. Everything is going to be transparent, and you have to get used to it, you have to behave accordingly. It becomes, how should I put it, integrated into your personality, but if you have nothing to hide, you shouldn’t be afraid.”
How are bank systems like the SWIFT Network secured? I ran into someone who had worked for SWIFT, traveling the world installing network and security software at banks who were joining their network. She told me that she had two handlers; one from NSA, the other from the CIA. Each spy watched over her and the other spy to be sure no one was putting anything malicious into the system. After all, spies and bankers trust no one, especially not spies nor bankers. They were using special bank grade cryptography, which has far greater security than the public is permitted to use. This also shows the level of cooperation between banking and spying, something discovered early on by the Rothschilds.
Commercial services must exist in the “Bank” level or below. Operate a “weapon” level service and you will be out of business. “Military Grade” means the military and others can get in — the data is fully transparent to certain groups but not to anyone else. Big Tech lives in the Open Source world, where software is engineered to solve problems while collecting your data at the same time.
The Myth of VPN’s
What about VPN’s? They are not as private as you think. When I tell people this, you can see the sadness in their eyes…they truly believed they actually had privacy. Sorry for that.
A friend who consults on these matters had done research on VPN’s and he shared some information with me (paraphrased from his email to protect his confidence):
Research using tools like DNSlytics, Netlas, and others suggest
that more than 65 percent of VPN operators use the M247 infrastructure
for end points from VPNs. Customers include several famous internet brand names we will not mention here, NOTE: if you carefully examine the egress points of your VPN, you should be able to see if they use M247.The M247 operates primarily out of Bucharest, Romania. A map
of the firm's "servers" and "points of presence" is available at LINK and HERE.In October 2016, Metronet acquired M247, for about US$52 million LINK. People running Metronet came from UK telcos. It is important to note that UK based telcos and ISPs allegedly cooperate fully with the UK National Crime Agency and GCHQ (UK’s version of NSA).
NOTE: Once the USA, UK, Israel, Japan, Australia, Canada and New Zealand have something, they all have access to it. It’s no longer FIVE EYES, it’s now SEVEN EYES.
At Unseen we built a hardware based VPN. Within a year of release, these were banned in China and Russia — I guess that means they worked. One of our customers told us our hardware VPN was the only VPN he couldn’t detect and he had tested 60 VPNs. Everyone else used standard OpenVPN and other software tools that left clear signatures in the data, which is how they were detected. There’s a very good chance we might bring something similar to this to our network.
Regular VPN’s dump you out on the Internet in other places and countries. You are still facing the same spying and threats of the internet when using a VPN because you are again on the open internet. Only when you connect directly to a server itself are you secure.
Please Take Our Survey so we can Build the Safest Way to Communicate (that’s publicly available). It takes less than 5 minutes and your answers are confidential. We appreciate your help!
CLICK HERE
Secure Messengers
Signal users went into a tizzy when the CEO of Signal started begging for money because the main source of funding for them was a branch of the US government and it was drying up. The US government doesn’t spend money unless it achieves their goals and I believe these were related to giving secure comms to certain overseas groups who were opposed to their local governments. It’s also a handy honeypot for domestic security, as well. Their annual budget for personnel was about $19m for about 50 staff LINK, in addition to hosting and storage costs. That’s about $380,000 per employee. We should all wish to work at Signal, LOL. There are a number of eye-openers on that blog post from Signal.
Here’s a video you need to watch, if you use We Chat, Signal or Telegram. It’s a person speaking to the Scottish parliament and most who see this have a sudden epiphany, like finding out Santa isn’t real:
The shock was apparent from everyone I sent this video to admitting that the government (and implying all of them) have access to these messages.
I don’t need to say another word about secure messengers, since this is right from the horse’s mouth. Apparently, end to end encryption and everything else about these messengers was a joke.
Hardware, Software and Networks
Hardware is nearly all corrupted in several places. The most obvious is the CPU — all major CPU’s have an administrative section which has God mode powers along with wifi and 3G access built in, separate from the wifi, cellular or ethernet access. Originally installed in x86 processors, this is now a “feature” of all current CPU’s, though it might not be called Management Engine.
Here’s an article that discusses the “Management Engine” back door:
The EFF described Intel ME as a “largely undocumented master controller for your CPU: it works with system firmware during boot and has direct access to system memory, the screen, keyboard and network.”
Back in June 2016, hardware hacker Damien Zammit warned, “Recent Intel x86 processors implement a secret, powerful control mechanism that runs on a separate chip that no one is allowed to audit or examine. When these are eventually compromised, they’ll expose all affected systems to nearly unkillable, undetectable rootkit attacks.”
Translation: someone with access to this God mode basically owns your computer and can see and hear everything happening on it. All major CPU’s have this “feature”. ARM, inside your phone, AMD and of course Intel Inside. Intel processors have had hidden wifi and 3G connections for many years.
Here are some general rules of thumb about Big Tech spying:
-Assume your phone is always listening. Google spies on everything you say. I’ve personally experience talking with my Android phone in my pocket about pouring a concrete pad and 20 minutes later got ads for concrete pads when I went back inside. All Big Tech does this. Taking your battery out used to be an easy way to stop this when you needed more privacy, but batteries are no longer removable. That was handy for Big Tech, wasn’t it?
-Most devices with electricity could be used for eavesdropping and they connect via cellular IoT bands. IoT is the last unregulated area of the internet and it has billions of devices connected to it. This includesTV’s (which have both cameras and microphones), ovens, washing machines, stereos, etc.. Eavesdropping can be done remotely or through apps on your device. In the case of TV’s the easiest fix is to put a piece of tape over the camera. The microphones used in these devices are dirt cheap, so they will be put everywhere. A friend with a relative at a Chinese security agency told me they can hear ten offices away through a phone microphone. It’s not only your devices spying on you, it’s everything else around you.
-Avoid electronics made by Chinese firms. Here is one case of a clothes iron that had a wifi hacking device inside that sends spam and malware to your network LINK.
-Disable anything with Google. Apple is a little better, but since Steve died, many things he would have forbidden have no doubt been compromised.
The internet is a collection of private networks connected to each other. Everything works well, as long as everyone cooperates. In unstable times, however, things start to break down and it’s time to “lock the gate”.
Policies of each network affect what you can do on the network and this is becoming a problem with de-platforming and censorship. Additionally, the openness of the networks allow security agencies, Big Tech and hackers to collect data and censor data easily. One way to do this is to hack an existing router, or in the case of security agencies, to install a router in line at the data center. We saw this at Xoom.com in 1997, with a special NSA room at our ISP that was collecting all email and web site visits. No one is the wiser while everything is vacuumed up — and of course the ISP is paid well for this service. No one knows where all that data goes, as it’s shared among different agencies who no doubt trade it with others and even sell it for profit.
The Internet is Becoming Adversarial
The internet has become adversarial and most of the threats you need to worry about are on the public internet. What is not well known is we are entering the next phase of the information war which involves the direct censorship and the altering of information. If you can’t get a message through in the first place, whatever level of security you have on that message is worthless. What is needed is a private network for Anti-censorship and the network is the key to getting your message through.
Routers carry your information and because they are exposed to the public internet, they are a major potential problem, as this screen grab shows. In 2014, Edward Snowden talked about router hacking and toolkits that allow access to Quality of Service (QoS) settings inside the router and many other functions. Just hack in and lower the QoS and you can block access to a web site, like this screenshot demonstrates:
This is an MTR chart, it shows the path of packets of information from your computer to the server you are trying to reach. In this case, two routers at Hurricane Electric in California, which is alleged to be affiliated with the CCP, dropped 75% and 89% of the packets, making communications impossible. This kind of attack destroyed Unseen — customers could not reach our server and they requested refunds. You should expect to see missing email, phone calls and blockages to become more frequent.
Big Tech Spying is Ubiquitous
A friend who is a contractor for Google told me Google does not allow their vendors to use Gmail and other public facing services when communicating with Google. LOL! I guess the spying is so bad they won’t even use the services themselves.
Data is collected from the entire internet by Big Tech. No one has any idea what it is exactly used for or who it is shared with. Here are some examples of data collection you might not be aware of:
CAPTCHA - those cute grids that have become popular memes, they collect your IP address every time you solve them.
CAPTCHAS are ubiquitous to the point they are now used for jokes.
fonts - collecting your IP from every web page the fonts are on.
DNS (Google and Cloudflare)- collecting your IP and sites you visit
Open source software - has had trackers installed. Where are the code reviewers?
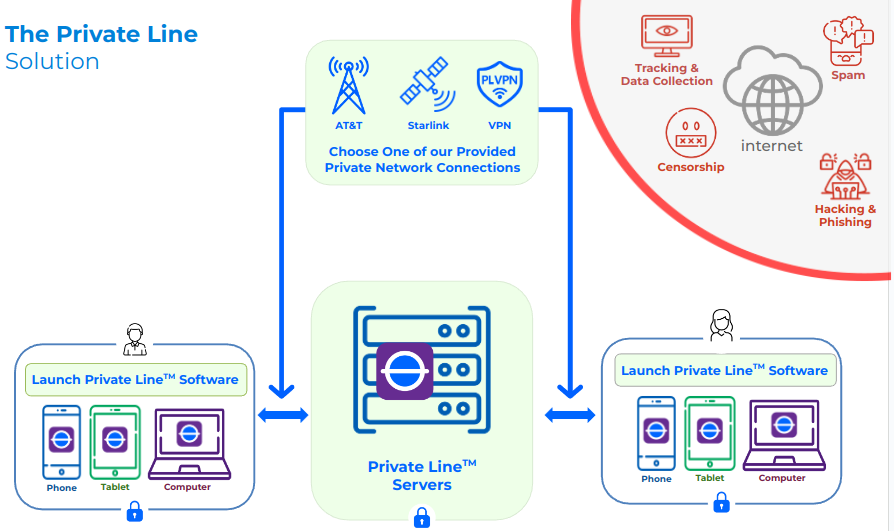
Private Networks Will Play a Key Role in Your Personal and Business CyberSecurity
Here is the big picture:
Existing devices such as cellular phones, laptops and desktop computers can access Private Line’s enclave for services such as private chat, calling and file sharing, as well as other applications like crypto wallets, financial applications, marketplaces and forums. All are sequestered inside the firewall and are not accessible to the public internet. Away from threats of the internet and Big Tech.
If things become bad on the Internet, we will build our own private Internet for our clients, colleagues, friends and family. A place for members only, with our own terms of service, privacy policies and without censorship. We call it Private Line and we hope you will come along for this exciting journey!